Find out how Reco keeps Microsoft 365 Copilot safe by spotting risky prompts, protecting data, managing user access, and identifying threats – all while keeping productivity high.
Microsoft 365 Copilot promises to boost productivity by turning natural language prompts into actions. Employees can generate reports, comb through data, or get instant answers just by asking Copilot.
However, alongside this convenience comes serious security concerns. Copilot operates across a company’s SaaS apps (from SharePoint to Teams and beyond), which means a careless prompt or a compromised user account could expose troves of sensitive information.
Security experts warn that organizations shouldn’t assume default settings will keep them safe. Without proactive controls, every file in your organization could be accessible via Copilot. A malicious actor might use Copilot to discover and exfiltrate confidential data without having to manually search through systems.
With the right prompts, an attacker could potentially locate sensitive files or even map out IT infrastructure and vulnerabilities. To safely embrace Copilot’s benefits, companies need equally innovative security measures.
Reco’s Approach to Microsoft Copilot Security
Reco, a SaaS Security platform, steps in to address these Copilot-induced risks. Unlike traditional security tools that might overlook in-app AI activity, Reco takes a holistic approach to secure Copilot. It treats Copilot as another component of the SaaS ecosystem that needs monitoring and governance – much like an additional user or app that touches your data.
Reco’s platform continuously analyzes how Copilot interacts with your organization’s SaaS data and users, providing real-time detection and insights that would be impossible to get from Copilot’s native settings alone.
Reco’s strategy for Copilot security covers six key areas. Here’s a breakdown of each of these areas.
Prompt Analysis
One of the most novel parts of Reco’s approach is analyzing the prompts (queries) that users input into Copilot. After all, Copilot will do whatever a user asks – so if someone asks it to do something questionable, Reco aims to flag that early.
Reco uses a multi-phased prompt analysis approach that evaluates every Copilot query against several criteria. Some key elements of this analysis include:
1. User Context
Reco links each Copilot prompt to the specific user’s identity and role. The same query that might be normal for an IT administrator could look very suspicious coming from a sales or finance employee. For example, if an HR intern starts querying network configurations via Copilot, that’s a red flag, whereas an IT engineer asking the same question might be within their job scope.
2. Keyword Detection
Reco monitors Copilot prompts for sensitive keywords or phrases that often indicate risky behavior. If a user query includes terms related to confidential data types (like “SSN”, “credit card”, or other PII), or hacking/abuse keywords (like “bypass authentication” or “export user list”), Reco will flag it. This acts as a first line of defense; any attempt to directly request sensitive info via Copilot triggers an alert.
3. Context Analysis
Malicious or careless Copilot prompts aren’t always obvious (“export all customer credit card numbers” is a clear red flag, but an attacker might be more subtle). A clever prompt could coax Copilot into revealing sensitive data without using any blatant keywords.
That’s why Reco applies natural language processing (NLP) to understand the intent behind the prompt. This catches cleverly worded queries that avoid obvious keywords but have the same dangerous intent. For example, instead of using “password,” someone might ask, “how does the login system work internally?”
4. Attack Pattern Matching
The platform compares prompts against known attack techniques from frameworks like MITRE ATT&CK. Using vector similarity matching, Reco identifies when a query resembles a known malicious pattern, helping catch advanced attempts where Copilot is used as a reconnaissance tool.
Data Exposure Management
While prompt analysis watches what users ask, Reco also monitors Copilot’s responses and actions—particularly those that might expose data improperly.
Reco tracks file-sharing and link-sharing events involving Copilot. If Copilot generates content that gets shared, Reco verifies the sharing permissions align with security policies. For instance, if a Copilot-generated document is made publicly accessible, Reco flags this as a potential risk.
The platform also integrates with data classification systems (like Microsoft Purview sensitivity labels) to understand what data Copilot accesses. When Copilot interacts with content categorized as sensitive or confidential, Reco logs these events and generates appropriate alerts.
Identity and Access Governance
Securing Copilot requires ensuring only appropriate users have access and that they operate under the principle of least privilege. Reco continuously analyzes your SaaS user base to identify identity risks that Copilot could amplify:
- Accounts with excessive permissions that could use Copilot to access massive amounts of data
- Users lacking multi-factor authentication who present higher compromise risks
- External accounts or stale accounts that might inappropriately access Copilot
- Suspicious access patterns that could indicate compromised credentials
By identifying these issues, Reco helps organizations maintain proper access controls around Copilot usage, preventing it from becoming a tool for unauthorized data access.
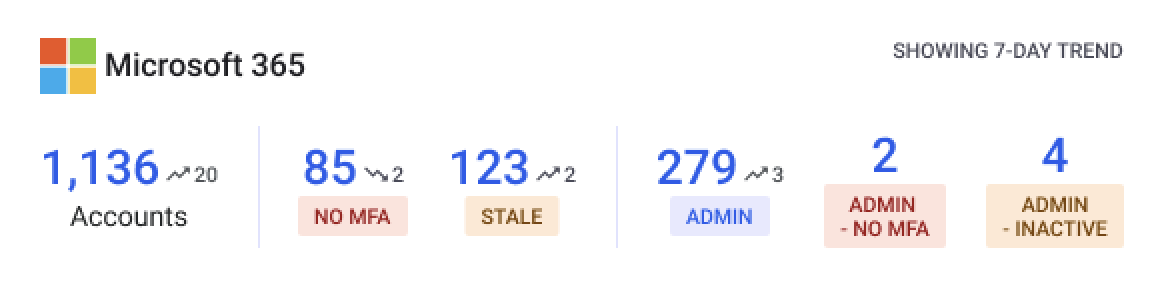 |
| Reco’s identity risk dashboard for Microsoft 365 |
Threat Detection
Reco treats Copilot interactions as a security telemetry stream that can reveal suspicious behavior, when correlated with other data points about a user. The platform flags indicators of potential attacks:
- Unusual access locations or suspicious IP addresses for Copilot sessions
- Abnormal usage patterns, such as excessive data retrieval or off-hours activity
- Potential insider threats, like an employee using Copilot to download unusual volumes of confidential documents
- Sign-in anomalies that could indicate account compromise
Each alert includes contextual information mapped to frameworks like MITRE ATT&CK, helping security teams quickly understand and respond to potential threats.
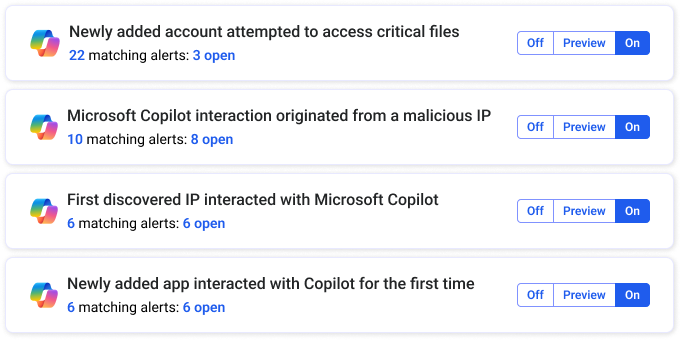 |
| Reco generates Copilot-specific alerts |
Direct Visibility
Reco addresses the visibility gap many organizations face with new AI tools like Copilot through its knowledge graph that visualizes usage across your SaaS environment. This graph:
- Shows who is using Copilot and what data they’re accessing
- Identifies anomalies in usage patterns
- Connects activities across your SaaS stack for contextual understanding
- Tracks trends in Copilot adoption and utilization
This bird’s-eye view helps security teams identify potential risks and inefficiencies, such as an unusual concentration of Copilot queries targeting confidential information or external accounts invoking Copilot inappropriately.
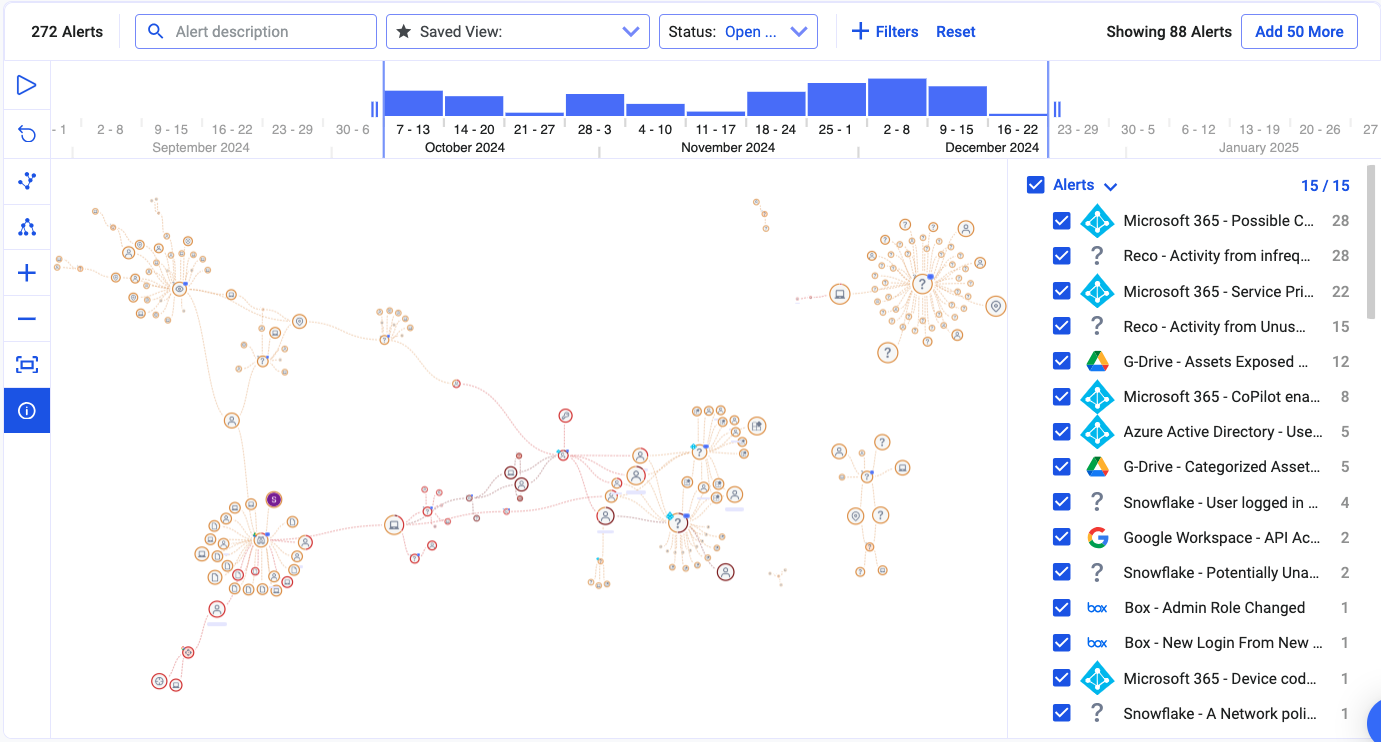 |
| Reco’s knowledge graph |
SaaS-to-SaaS Risk Detection
As organizations integrate Copilot with other applications, new risks can emerge. Reco monitors cross-application interactions where Copilot connects with other SaaS tools.
The platform detects when new applications appear and interact with your environment through Copilot, flagging shadow AI or unsanctioned integrations. For instance, if a developer adds a plugin that connects to Copilot without security team approval, Reco brings this to light immediately.
What Reco Does Not Do for Copilot Security
To set appropriate expectations, it’s important to understand Reco’s boundaries:
- Not DLP or Content Filtering: Reco doesn’t block or censor Copilot outputs in real-time—it alerts and logs concerning events rather than preventing them.
- Not Endpoint Security: Reco operates at the SaaS layer, not at the device level. It complements but doesn’t replace endpoint protection.
- Not Configuration Changes: Reco will flag a misconfiguration, but it doesn’t modify Copilot settings. While you can raise a ticket to the app owner through Reco and provide remediation instructions, you’ll still have to use Microsoft’s tools to configure the service.
Conclusion
As we’ve explored, Copilot can potentially touch everything – all your documents, messages, and data – which is both its strength and its biggest risk. Securing Copilot is therefore not just about Copilot itself, but about securing your entire SaaS environment against a new kind of access and automation.
Reco’s dynamic approach to Copilot security can help organizations embrace these AI tools safely.
To go deeper into this topic and get concrete guidance, we recommend downloading the white paper Secure AI Copilots and Agentic AI. It offers best practices on governing AI copilots and detailed insights on strengthening your SaaS security posture in the age of AI.
