I published on the 29 Apr 2025 a diary [1] on scanning activity looking for SonicWall and since this publication this activity has grown 10-fold. Over the past 14 days, several BACS students have reported activity related to SonicWall scans all related for the same 2 URLs [4][5] previously mentioned in my last diary. My own DShield sensor was probed by 25 separate IPs during those last 14 days. The three most active IPs were all from the same subnet – 141.98.80.0/24
Activity by URL
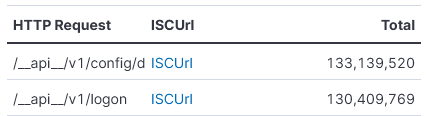
Indicator
185.193.88.229
185.193.88.178
185.193.88.223
141.98.80.125
141.98.80.126
141.98.80.118
92.63.196.249
92.63.196.152
80.82.65.127
45.146.130.12
[1] https://isc.sans.edu/diary/Web+Scanning+Sonicwall+for+CVE202120016/31906/
[2] https://es-la.tenable.com/blog/cve-2021-20016-zero-day-vulnerability-in-sonicwall-secure-mobile-access-sma-exploited
[3] https://cow-prod-www-v3.azurewebsites.net/publications/security-advisories/2021-006/pdf
[4] https://isc.sans.edu/weblogs/urlhistory.html?url=L19fYXBpX18vdjEvY29uZmlnL2RvbWFpbnM=
[5] https://isc.sans.edu/weblogs/urlhistory.html?url=L19fYXBpX18vdjEvbG9nb24=
[6] https://www.sans.edu/cyber-security-programs/bachelors-degree/
———–
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
